| Protecting Optical Networks from Disruption | |||||
|
Source: David R. Goff. Fiber Optic Video Transmission, 1st ed. Focal Press: Woburn, Massachusetts, 2003 and other private writings. |
|||||
|
Technology Basics
Modern society is highly completely dependent on communications technology. Network failures, whether due to human error or faulty technology, can be very expensive for users and network providers alike. As a result, the subject of so-called fall-back mechanisms is one of the most talked about in the communications industry. A wide range of standardized mechanisms is incorporated into synchronous networks in order to compensate for failures in network elements.
Two basic types of protection architecture are
distinguished in APS. One is the linear protection mechanism used for
point-to-point connections. The other basic form is the so-called ring
protection mechanism which can take on many different forms. Both
mechanisms use spare circuits or components to provide the back-up path. Linear Protection
1:N Protection
|
|||||
|
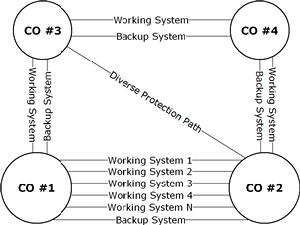
Figure 1 shows an example of 1+1 APS protection, 1:N protection, and diverse protection path. The 1:N protection scheme is shown between CO #1 and CO #2. There are N working systems (usually a pair of optical fibers, one for each direction) and a single backup system (usually a single pair of optical fibers, one for each direction). If any of the systems from 1 to N fail, the traffic that would normally be carried by that system is switched to the backup system.
One additional example of a protection strategy is shown on Figure 1. A backup system is shown between CO #3 and CO #2. The idea here is that this backup fiber runs along a different path than the normal working and protection fibers. This is a hedge against an event that may sever all fibers between two locations. |
Figure 1 - Examples of SONET Protection Strategies |
||||
| Return to Top of Page | |||||
|
|||||